Software Vulnerability Management
Firms and governments are increasingly concerned about cyberattack risks, in which malicious actors exploit software vulnerabilities. In Navigating Software Vulnerabilities: Eighteen Years of Evidence from Medium and Large US Organizations (NBER Working Paper 32696), Raviv Murciano-Goroff, Ran Zhuo, and Shane Greenstein document the widespread use of server software with known vulnerabilities and examine why organizations are slow to adopt updates.
The researchers focus on organizations using the Apache HTTP Server, a popular open-source web server software product. Users report potential vulnerabilities to Apache, which deploys a team of security experts to vet these reports. Once developers craft a fix, the vulnerability is publicly disclosed and the fix is released in a new version of Apache. Users must update their software to fix the vulnerability. During the period of study, 2000 to 2018, there were 158 vulnerabilities, of which 28 were severe, and 115 vulnerability-correcting software updates. These updates include information on corrected vulnerabilities and new features. Additionally, the Apache Software Foundation and the National Institute of Standards and Technology provide information on each vulnerability’s severity, report date, public disclosure date, and update release date.
Among organizations that use the Apache HTTP Server, in an average month, 68 percent are operating with known severe security vulnerabilities.
The researchers analyze organization-level information in the Bureau van Dijk Mint Global database. Each organization’s URL is matched to the Internet Archive Wayback Machine’s historical website information, which includes the host IP address, record date, and often the name of the server software and the software version number. In an average month, 68 percent of the organizations in the data sample operated with a known severe security vulnerability. This was usually due to failure to update: 57 percent used software with severe vulnerabilities even though updated, secure versions were available. New users of Apache — who likely started by installing a recent version of the software — were almost 12 percent less likely to be using software with a severe vulnerability.
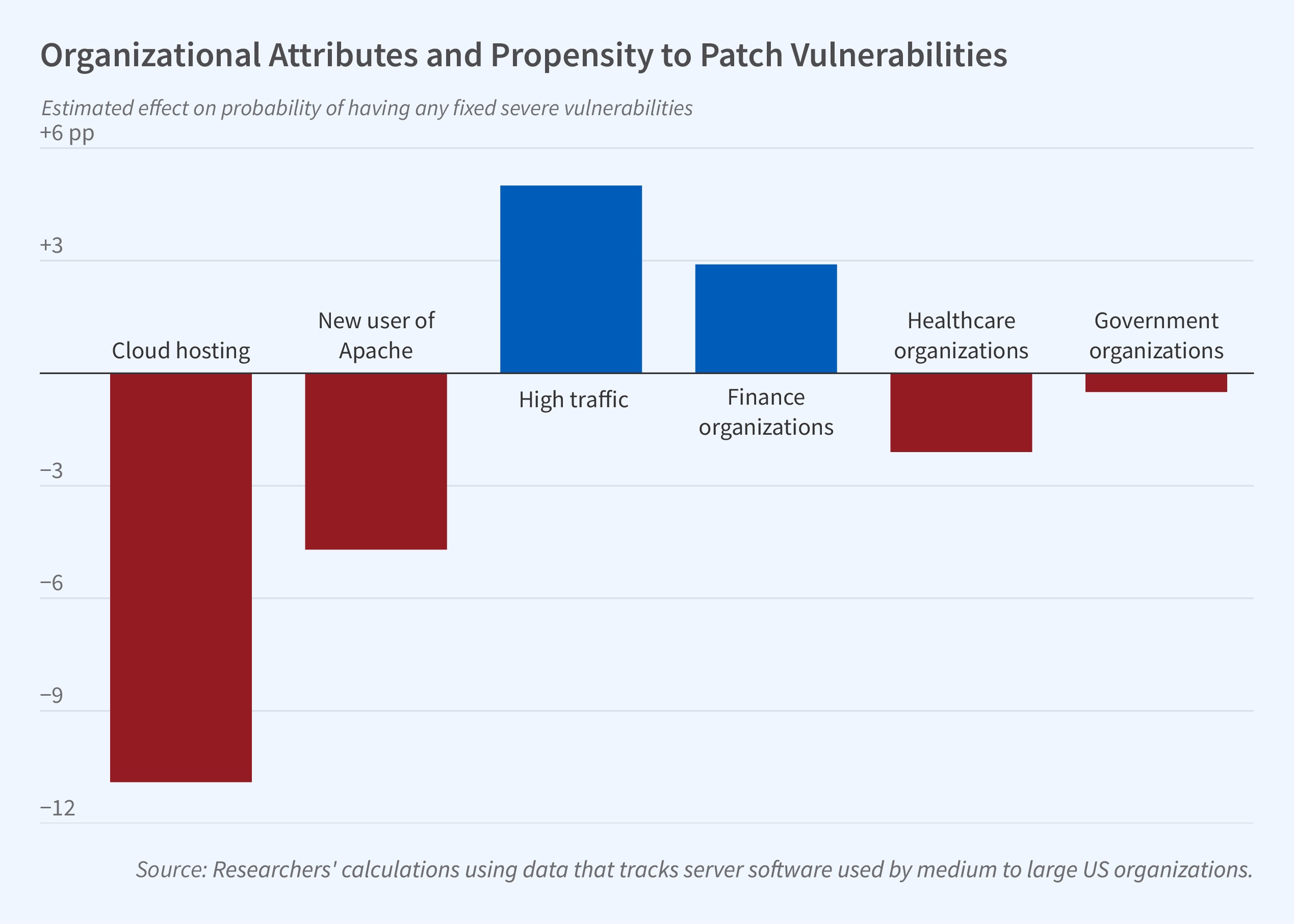
Cloud hosting can reduce an organization’s costs of updating since the host usually offers various types of support for vulnerability and update management. Organizations that use cloud hosting, identified by a website IP address from Amazon Web Services, Microsoft Azure, or Google Cloud, exhibit between an 11 and 20 percent lower probability of having fixable severe vulnerabilities. Those that outsource IT operations, as recorded by Harte Hanks, are also less likely to have fixable vulnerabilities.
The researchers also study some organizational risk factors and find little relationship between these factors and the presence of severe vulnerabilities. High-traffic websites are more likely to have fixable severe vulnerabilities. There is no consistent relationship between an organization being in the finance, government, or healthcare sector, or in a state or industry that recently experienced a data breach, and vulnerabilities.
Organizations do update more quickly when there are more severe vulnerabilities in a new release. However, they update more slowly when releases address additional nonsevere vulnerabilities or contain feature changes. They appear to be more responsive to updates in minor than major version releases.
These findings suggest that quick and compulsory disclosure of all vulnerabilities may benefit malicious actors more than organizations with vulnerable software, given delays in updating, and that standalone patches for severe vulnerabilities may be adopted more quickly than patches that are bundled with other fixes or feature updates.
—Whitney Zhang
The researchers thank Harvard Business School and the Ewing Marion Kauffman Foundation for funding this work.


